Security in Obscurity
A thought by Jeff Stein
Exploiting networks with ARP Poisoning
The ARP protocol can be used by an attacker to manipulate the network traffic sent between system, July 2020
The Address Resolution Protocol (ARP) is a network protocol used by a router to map layer three IP addresses to layer two MAC addresses for systems communicating on the network. The records stored by the router are held in the form of a table (ARP table) that allows the router to more quickly identify where to send network traffic. Given the inherent trust a system will place in network equipment and the information provided by it, the ARP protocol can be used by an attacker to manipulate the network traffic sent between system.
How it works
The router typically relies on ARP broadcast packets to populate the ARP table. This information is then used to properly route traffic across the network. The router will broadcast the requests to systems on the network to provide the matching information which the router is looking for and the system that contains the information in question will submit it to the router. The router will then store the information in a cache in the form of the ARP table for future use so that broadcasts are not needed each time traffic is router to an identified system.
How to exploit ARP
To take advantage of the ARP protocol an attacker will send false ARP messages over the network to "poison" the cache containing the ARP table with bad information. The objective of the ARP poisoning is to link an IP address of a victim to the attacker's MAC address so that traffic being sent to the victim will be routed to the attacker instead. The use case for this type of attack is to steal data meant for a victim. The main way that this attack can be implemented is a man-in-the-middle attack in which the attacker will insert themselves in between two legitimate hosts and send traffic back and forth between them, collecting all of the data along the way. This can yield a variety of information including account credentials and sensitive data types. Below you can see an diagram illustrating where the attacker will sit in the man-in-the-middle attack:
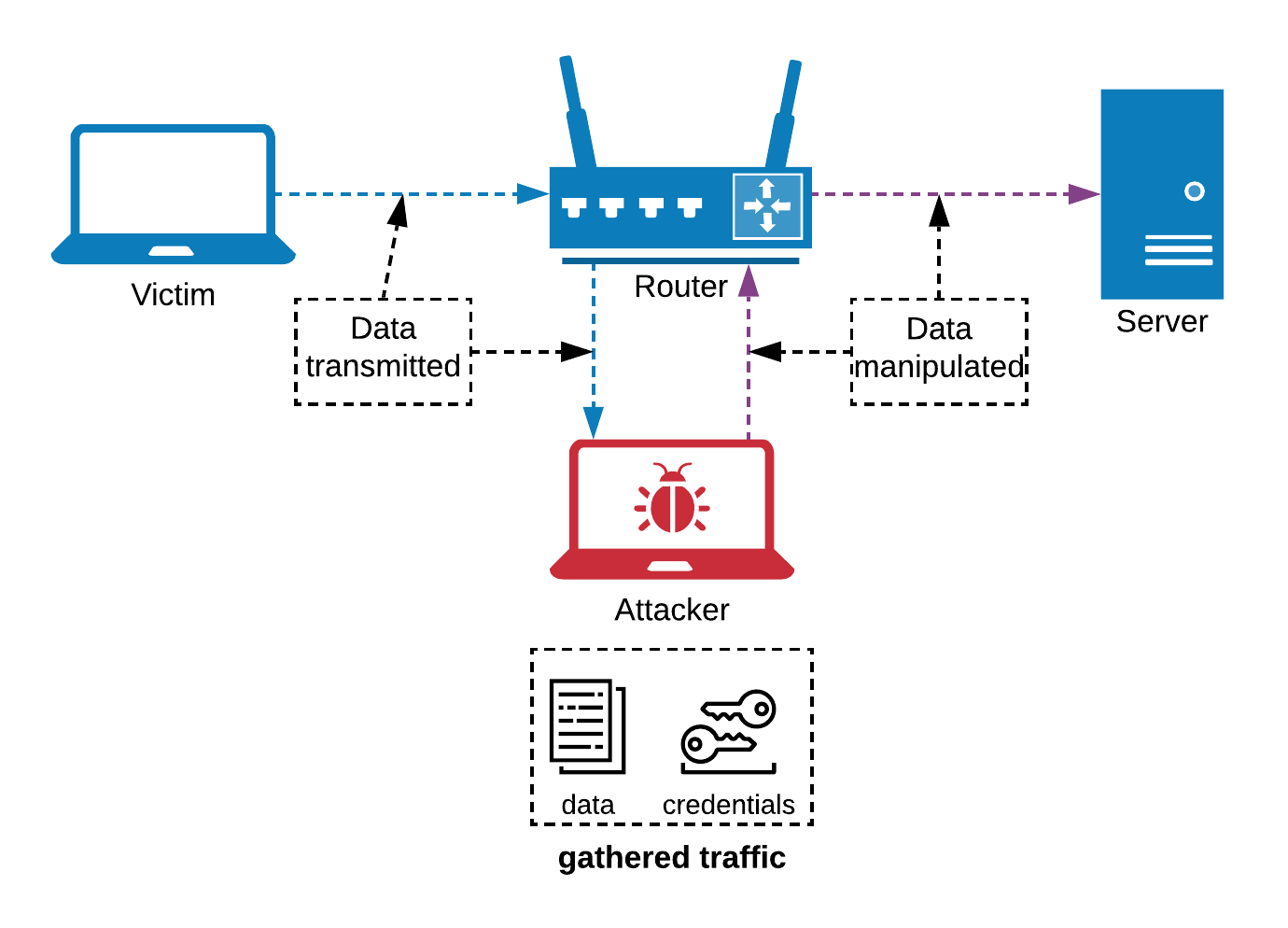
Using Cain to Perform a Man-in-the-Middle attack
One tool that can be used to perform a man-in-the-middle attack using ARP poisoning is Cain. Cain is one part of the Cain & Abel toolset which is a tool for the Windows operating system that enables the manipulation of network traffic to identify weak or plain text passwords. Cain is used for password cracking and network-based activities while Abel is placed on a vulnerable system to enable remote access and execution of commands on the system.
Using Cain you can sniff the network to identify potential victims to target as well as perform some system enumeration to help in the identification of the right targets. Once you have identified the system you want to target with a man-in-the-middle attack you can use the ARP tab in Cain and add the device to initiate the Man-in-the-Middle attack against. To complete the process, Cain will then give you an option to select a second system to gather traffic between.
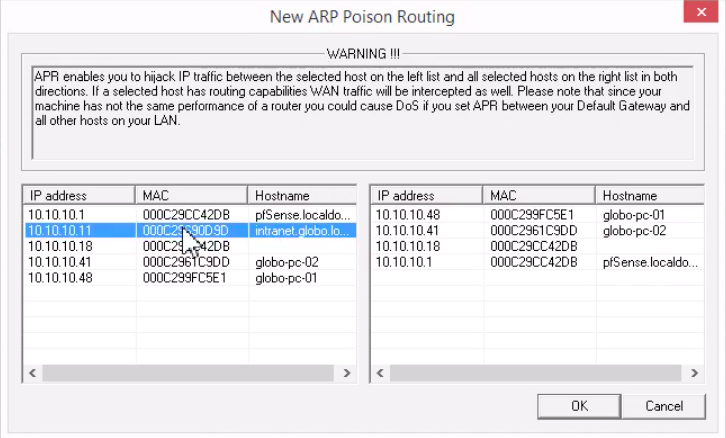
Once you have your attack initiated, you will start to see packets being captured by Cain, between your targeted systems.
Cain will collect a variety of network information, especially any credentials being submitted between the systems. This information can then be used to continue an attack against a victim. If you are interested in learning more about Cain and the tools many use cases, you can check out my course, Credential Access with Cain & Abel on Pluralsight here.
When it comes to network equipment, the inherent trust systems place in gateway equipment such as routers can be exploited by attackers. One such aspect of network protocols that can be used by a malicious actor in their attack is the Address Resolution Protocol. By spoofing the information collected by an ARP table an attacker can not only poison the table but also create the ability to perform a man-in-the-middle attack to gather valuable information which a victim is sending over a network.
Tags
Security Vulnerabilities IDS/IPS Malware Ethical Hacking Policies PowerShell Python Splunk Network Security Script PKI Firewall Router Vulnerability Management



