Security in Obscurity
A thought by Jeff Stein
Exploiting WiFi Direct
While WiFi Direct is billed as a secure method for connecting to IoT devices using it can be risky, October 2019
WiFi Direct is a wireless standard commonly used by many IoT devices including desktop printers as a way to offer convenient, wireless connections to the equipment. While WiFi Direct is billed as a secure method for connecting to IoT devices using the "latest WiFi security technology" i.e. WPA2, using WiFi Direct can be risky. [1] In particular, instances in which the WiFi Direct device is also connected to a wireless network, WiFi Direct can offer an avenue for an attacker to target the additional wireless network. For this thought, I have gone through a variety of attack scenarios on how WiFi Direct can be exploited.
About WiFi Direct
WiFi Direct works by establishing a private wireless network that a device can connect through for the purpose of performing peer-to-peer communication. It is convenient because it allows a device to communicate with an WiFi Direct enabled system without connecting cables. All that is required to connect is to make a wireless connection request to the WiFi Direct device and have the request accepted. This works similar to WPS in which a pin is used to authenticate the device attempting to connect. Another comparison to how the connection of WiFi Direct works is to that of a Bluetooth connection being made between a phone and a Bluetooth enabled device. Once connected, the peer-to-peer network creates a WPA2 wireless network without requiring added infrastructure such as access points or event internet connectivity. Below is a diagram which illustrations the WiFi Direct connection process:
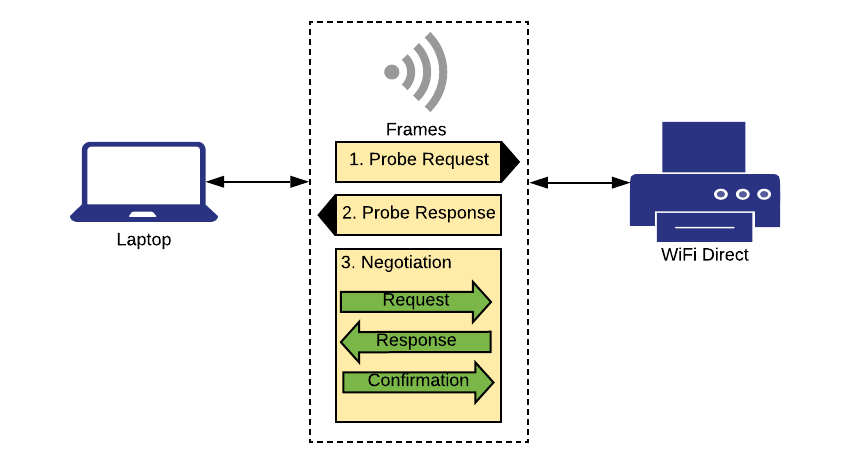
[2].
Limitations
Many of the issues related to WiFi Direct are associated with how vendors have chosen to implement the standard. Below are some of the main issues and limitations that you may run into when using a WiFi Direct enabled device.
Default Passwords
Creating simple pre-shared keys (PSK) which are used to facilitate a smooth user experience in connecting a device to WiFi Direct enabled equipment are common among vendors. In fact in reviewing support documentation from large printer manufactures I found the following vendors list the default WiFi Direct passwords for their devices publicly.
Concurrent Connections
Many vendors allow the WiFi Direct enabled devices to also connect to other LAN/WAN networks in addition to the peer-to-peer networks established through WiFi Direct. For all intensive purposes if a printer for example, is connected to a wireless network and WiFi Direct is also turned on in the settings, the device is now creating a rogue access point. This scenario makes a WiFi Direct implementation more risky because the device can now serve as a target for an attacker to attempt to pivot from the peer-to-peer network to the wireless network.
Access to data over air
This might also be viewed as reducing the risk associated with leveraging WiFi Direct due to a limit in range in which an attack may occur. I do think the idea that an attacker can access the data over air and target the device within a 200 meter radius should be considered a concern. [2] While the range of attack may be finite, it reduces the requirement for an attacker to be completely present physically, to take advantage of the attack methods related to WiFi Direct. To more easily attack WiFi Direct an malicious actor can leverage war driving techniques to effectively target your device.
Physical Access
Many of the IoT devices which support WiFi Direct tend to also have convenient physical screens or easily accessible menus which will display the WiFi Direct PSK in plain text. For example, on many printers you can print a configuration page while physically at the printer which will contain the WiFi Direct information as well as other important data such as the machine MAC address and IP address. Additionally, another networks the device may be connected to can be found on the config printout along with those MAC addresses and IP addresses. Using this information, an attacker can easily execute a physical attack against the device and potentially use the information to target other WPA2 networks.
Attacks
Taking advantage of the default key
If you have the default pre-shared key for the WiFi Direct network you can attempt to connect to the network as you would connecting to any other WPA2 wireless network. Once connected, you can use NMAP to scan the network to identify any devices and ports open. This will allow you to connect to any vulnerable devices, based on the results.
Brute Forcing a Pre-Shared Key
If the WPA2 PSK is not too complex, it may be brute forcible. To execute a brute force attack against the WiFi Direct network you will need to capture the handshake which occurs when a device communicates with the WiFi Direct network. This can primarily be done using a Kali Linux system with a wireless card. You will convert the wireless card to a listening device using a tool included in Kali Linux called airmon-ng which is contained in the aircrack-ng package. Start by identifying your wireless card in Kali Linux. From the terminal you can run:
Command
ifconfig
This will show you all of your network interfaces. More than likely your wireless card will be wlan0 or wlan1. Once you identify your wireless card you can turn it into a listening device running the following command in terminal where wlan0 designates your wireless interface found when running ifconfig:
Command
airmon-ng start wlan0
Running an iwconf command from the terminal will show that your interface is now in monitor mode and should display something like:
Example
wlan0mon
Now that you have a listening device on your system you can use airodump-ng, another package a part of the aircrack-ng suite of tools to gather packets off a WPA handshake occurring with the WiFi Direct device. Essentially you want to target the channel which WiFi Direct is broadcasting on (usually either 1, 6 or 11) and capture all of the packets between systems and the WiFi Direct device where the WPA handshake is negotiated for the WiFi Direct connection to be allowed. From the terminal run:
Command
airodump-ng -c 11 wlan0mon
In this command, 11 designates the channel the WiFi Direct network is broadcasting on and wlan0mon indicates your wireless listening interface. Replace these options with the channel and interface specific to your scenario.
Note that once you are done gathering packets you will want to convert your wireless card back to managed mode from monitor mode. The following two commands will accomplish that:
Commands
airmon-ng stop wlan0mon
service network-manager start
Once your packets are collected you can attempt to crack the pre-shared key of the WiFi Direct network using aircrack-ng. To crack a WPA2 PSK, a dictionary attack is required and used against the .cap file you have gathered containing the WPA handshake. This is a wordlist comprising of common pre-shared keys that you can submit against the WiFi Direct PSK to see if any words in the list can crack it. Kali Linux comes with a few wordlists by default including common.txt and rockyou.txt. Additional lists are available on the Internet or you can build your own to add custom words that might relate to the network you are trying to attack. To use aircrack-ng run the following from terminal:
Command
aircrack-ng [filename].cap -w [wordlist].txt
An alternative option to using the aircrack-ng suite of tools directly is to take advantage of another tool in Kali Linux called Fern Wifi Cracker.
Fern runs as a GUI application that leverages aircrack-ng tools in the background to perform your attack against the WiFi Direct network for you. The Fern tool will allow for point and click ability to execute an attack however I would still recommend to be familiar with the aircrack-ng tooling and process first-hand to understand what you are executing, against a wireless network. To access Fern Wifi Cracker run the following from a terminal in Kali Linux:
Command
fern-wifi-cracker
Pivoting to other networks
Once you have the pre-shared key for the WiFi Direct network you can try to target additional wireless networks which the device is connected to, in additional to the WiFi Direct network the device is broadcasting.
To take advantage of this attack you will want to leverage information about the IoT device that you can access once you are able to connect to the WiFi Direct network.
The information you should gather are:
1. The hardware MAC address for the NIC interface connected to any additional wireless network
2. The SSID of the additional wireless network
3. The channel the device is connected to the wireless AP
From Kali Linux you will need to modify the machine's MAC address to match that of the device you are trying to impersonate. This can be done from the terminal with the following commands:
Commands
ifconfig wlan0 down
ifconfig wlan0 hw ether 00:00:00:00:00:00
ifconfig wlan0 up
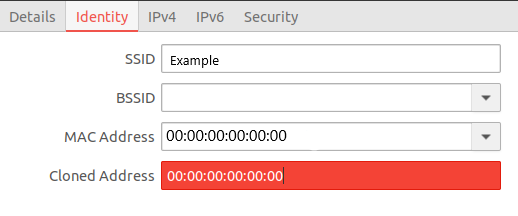
Once you have updated your wireless card to match the device you can connect to the SSID of the wireless network and add the MAC address to the "Cloned Address" in the Identify section of the wifi setup in Kali.
While WiFi Direct can be used as a convenient way to connect your device to IoT equipment such as printers and SmartTVs the standard may be exploited. While exploitation does require a physical presence of at least 200 meter to attack the wireless signal depending on the implementation of WiFi Direct the use case should be carefully considered. At the very least, connecting the WiFi Direct enabled device to other wireless or wired networks should be avoided and default passwords should be updated to something more robust.
Resources Consulted
[1] WiFi Direct (n.d.). Retrieved from Article Link.
[2] Blanco, Andrés. Attacking Wi-Fi Direct Protocol Implementations (2017). Black Hat EU17. Retrieved from Article Link.
Tags
Security Vulnerabilities IDS/IPS Malware Ethical Hacking Policies PowerShell Python Splunk Email Script PKI Firewall Router Vulnerability Management



