Security in Obscurity
A thought by Jeff Stein
Guide to counter denial-of-service (DoS) and DDoS attacks: Offsetting Risk with Cloud Services (Part 4)
This thought focuses on ways to offset the risk of a DDoS attack leveraging cloud services, August 2019
What can you do to counter a denial-of-service attack? There are a number of ways to counter denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks. This thought focuses on ways to offset the risk of a DDoS attack leveraging cloud services and is the final though of a four part series on countering DoS and DDoS attacks including:
Detection of Compromised Systems
Hardening of Systems to Block Infection
Remediating an Attack In Progress
Offsetting Risk with Cloud Services
Offsetting Risk with Cloud Services
Cloud computing offers a broad range of services to either replace traditional on-prem IT infrastructure or as new innovative solutions to complement your current technology stack. Leveraging cloud services as a part of your tech stack may reduce costs as well as potentially offset your business risk as it relates to security depending upon your unique business model. One example of a way that risk is commonly offset is by utilizing cloud services to address DDoS attacks. Below are some examples of cloud services which may help your business address DDoS threats.
WAF
A web application firewall (WAF), as the name implies, is a firewall specifically for your web applications. Like a traditional firewall, a WAF will analysis traffic to protect the web application from threats on the internet. The difference between a traditional firewall and a web application firewall is that a WAF focuses on HTTP/S traffic and shields the web application from a number of web attacks. Below is a diagram of how a WAF functions:
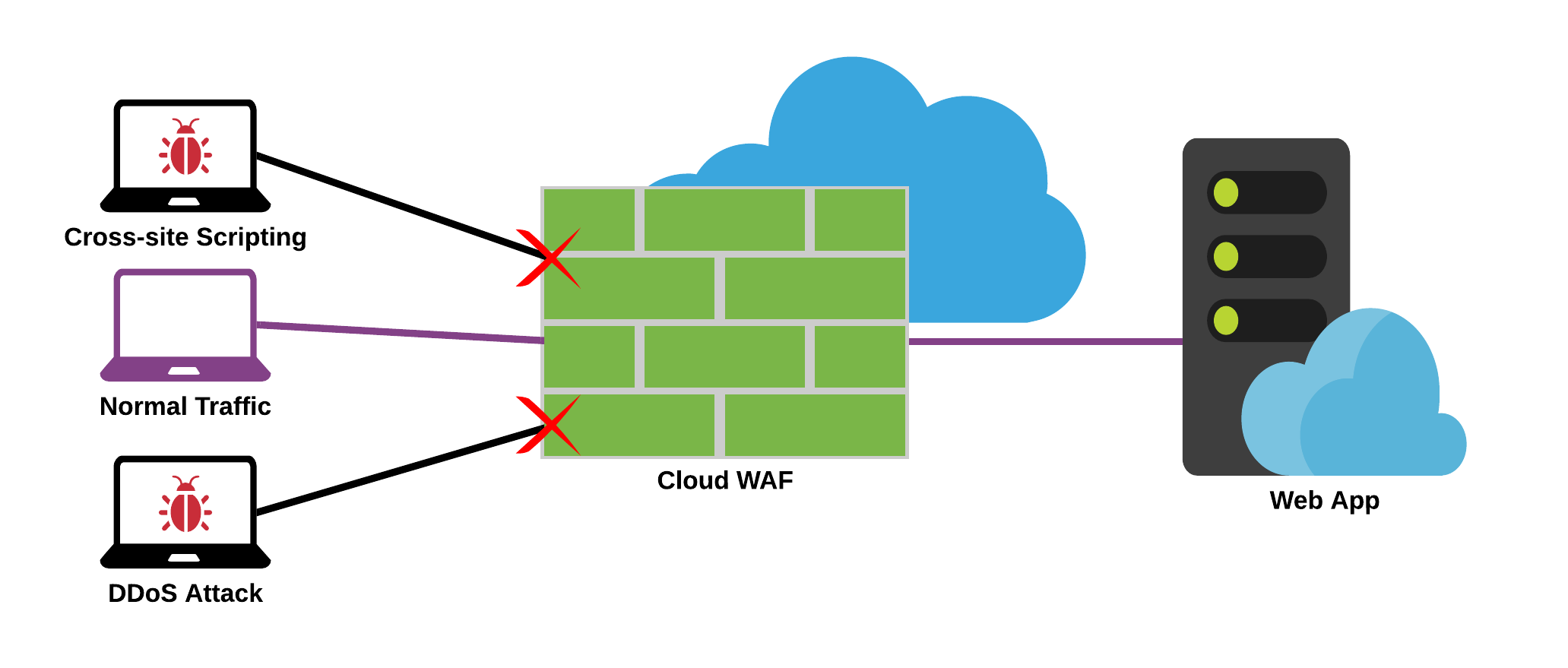
Common web threats such as Cross-Site scripting and DDoS attacks can be identified by a WAF and leveraged as a reverse-proxy for the web application to filter out the attacks as they happen. Many cloud providers such as Amazon offer WAFs as a service offering a part of their cloud portfolio. Additionally WAFs can be found as a SAAS offering by major market players such as Akamai.
To leverage a WAF, a number of configuration settings may be required. The most common change you will need to make regarding your web application is to shift the DNS records to the WAF cloud provider. This is required for the reverse proxy aspect of a WAF so that the cloud provider can successfully inspect traffic destine for your web application. Once the migration to the cloud WAF is complete you will be able to take advantage of the offerings provided by the cloud provider, offsetting some of the risk and the administrative upkeep required with managing physical equipment.
CDN
A content distribution network (CDN) is a service that enables you to distribution content at a global level. Rather than accessing the content on your website directly, the data is replicated to distribution points all over the world. When a visitor goes to access the content on your website they will be directed to the closest distribution point geographically to them rather than the site itself. There are a number of well-known cloud CDN providers such as AWS CloudFront as well as GCPs Cloud CDN.
Due to the nature of the CDN and the underlying distributed architecture, they can help relieve against DDoS attacks. A DDoS attack is successful when it overloads a webserver with traffic to the point that it is unable to server traffic to other requestors. Because CDNs are distributed, an attack against one node of the CDN will not bring down the rest of the nodes and the content being served. A CDN therefore makes the web content resilient against such attacks. The diagram below illustrates how a CDN works:
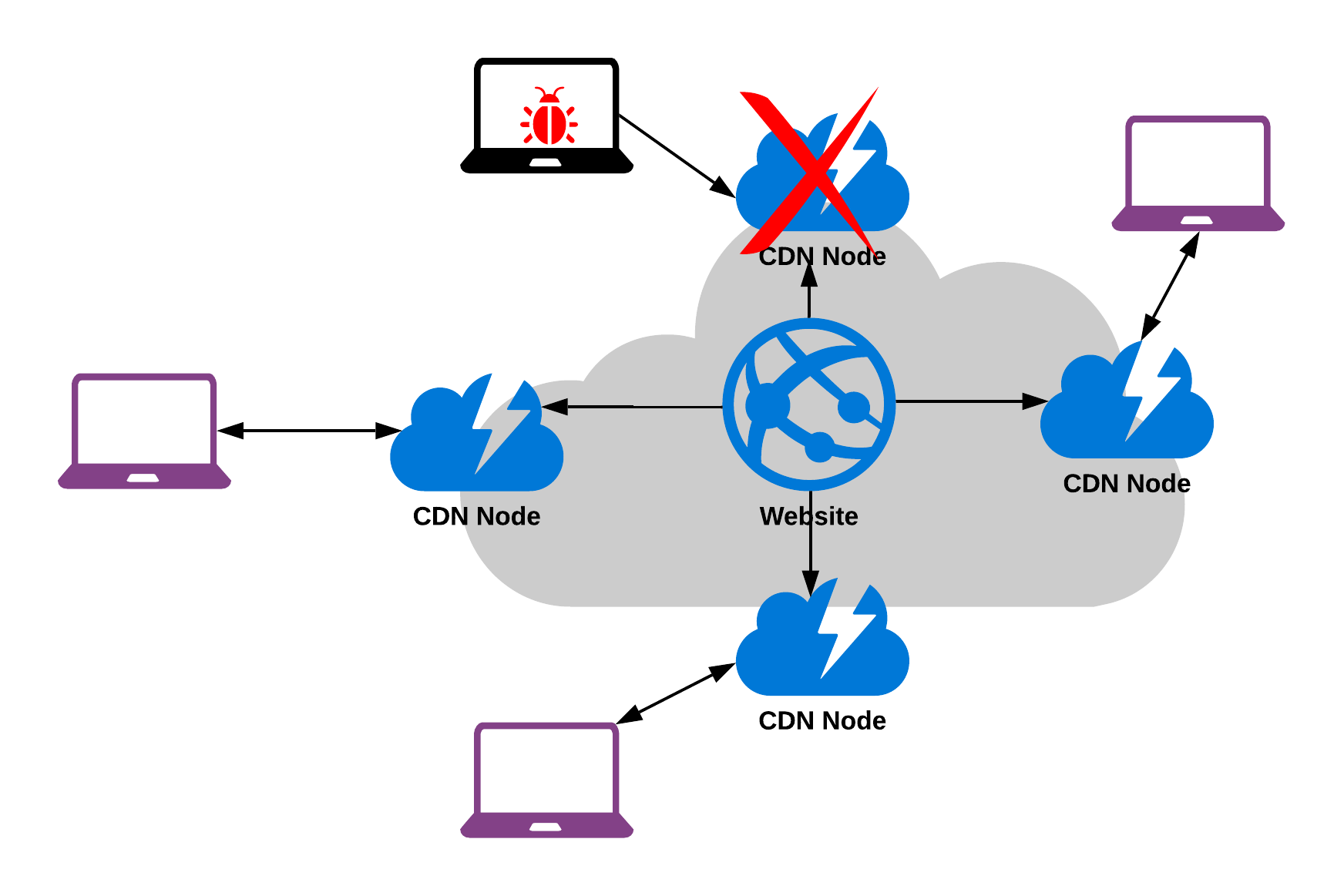
DDoS Prevention
A number of cloud services offer specific DDoS prevention. These solutions will require you to route your web traffic through the SAAS solution's proxy. Different methods to remediate DDoS attacks include network layer controls leveraging whitelists and blacklists as well as network control by region. Additionally, the solutions can offer rate controls which can limit the amount of traffic requests being accepted.
Vendors such as Akamai and Cloudflare offer services in this space. By leveraging a SAAS DDoS prevention solution you are able to rely on their economy of scale to more effectively handle DDoS attacks than in many cases you can address internally. This provides use cases to reduce time spent focusing on such attack scenarios and potentially offset risk associated with such attacks.
In summary, just as there are solutions on prem to combat DoS and DDoS attacks there are cloud solutions which offer many of the same features. These cloud solutions can certainly play a significant part in your overall DDoS prevention strategy with regard to your existing cloud web services as well as traditional web server designs. The overall cloud DDoS prevention solutions include those dedicated to DDoS attacks as well as more robust cloud offerings such as WAF's and CDNs. The benefits of cloud solutions vary with the approach but all can offer scalability as well as fast adaptability to the latest trends in cyber attacks.
Tags
Security Vulnerabilities WAF Malware Policies PowerShell Python Splunk Cloud Script PKI Firewall CDN Vulnerability Management



