Security in Obscurity
A thought by Jeff Stein
Securing your iOS device
Whether you are using your mobile device for work or personal use it is important to choose equipment that is secure, November 2019
Mobile devices continue to account for a growing share of the computer market not only in the consumer space but in the business world as well. Bring Your Own Device (BYOD) policies in work environments are typical and the uses for mobile devices have expanded beyond communication and internet access to handling confidential data such as online banking or document collaboration. Whether you are using your mobile device for work or personal use it is important to choose equipment that is secure. While the majority of the mobile market place is made up of a variety of android devices, I argue in this thought that you should consider using an iOS device when taking security into account. Additionally, beyond your equipment selection it is important to harden the OS configuration to reduce the likelihood that it can be exploited by a malicious attack.
Why an iOS phone is more secure than android
When assessing the security of iOS devices verses android and why the iOS operating system is more secure, it is important to understand how vulnerabilities in each ecosystem are addressed. Below you can see a diagram of how vulnerabilities are patched in iOS as opposed to android.
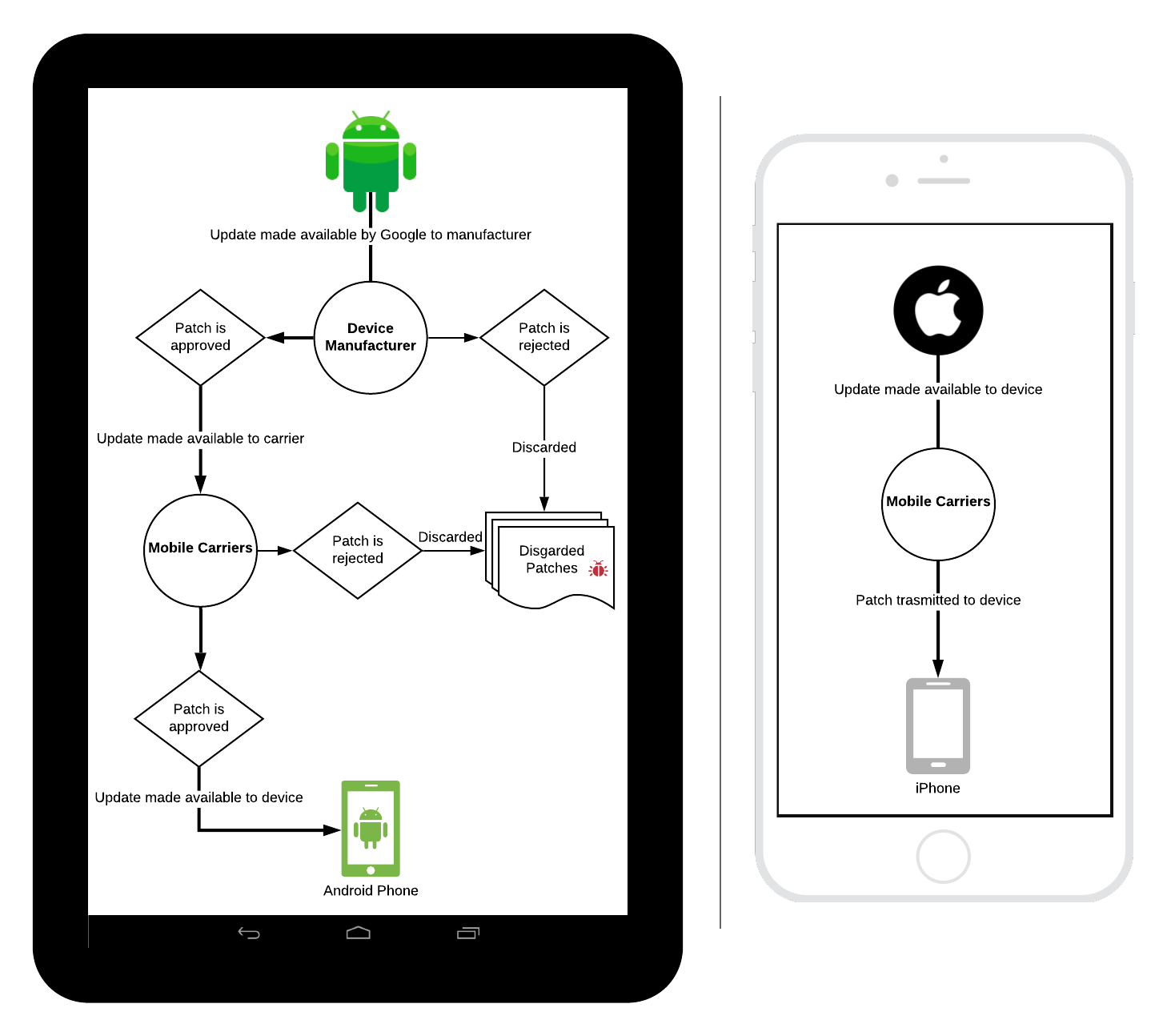
The above flows should clearly illustrate the difference between both operating systems. While Apple controls the entire ecosystem from hardware to the release of operating system upgrades on their device, android has a much different flow. In order for a device to be properly secured from known vulnerabilities against the operating system the patch must not only be made available by Google but also the phone manufacturers and the cell phone carriers. If at anywhere during that process the patch is rejected by the either phone manufacturer or the mobile carriers, the device will remain vulnerable even if the user is diligent in applying patches as soon as they become available [1].
The main reasoning behind the disparity between the two operating systems is the amount of control wheeled by Apple regarding iOS. Because it is a closed system they are able to control the device and in the carrier agreements as to what is placed on that device by mobile carriers. By comparison, android is an open-source OS which given both device manufacturers as well as carriers control over what is on the device. Hence you typically can see some "bloatware" on android devices placed there by either manufacturers, carriers, or both.
Features to configure
When using an iOS device I have identified a number of features the device and operating system provide that can be used to safeguard it. Taking advantage of these features can not only ensure you are protecting yourself but many of them should help improve the experience you have with the device as well. In the process it may reduce unwanted solicitations and improve your ease of use.
Table of Contents
Biometric
Block unknown caller feature
Disable not disconnect from WiFi and Bluetooth when not in use
Disabling iCloud by default
Disabling services invasive to privacy
Biometric
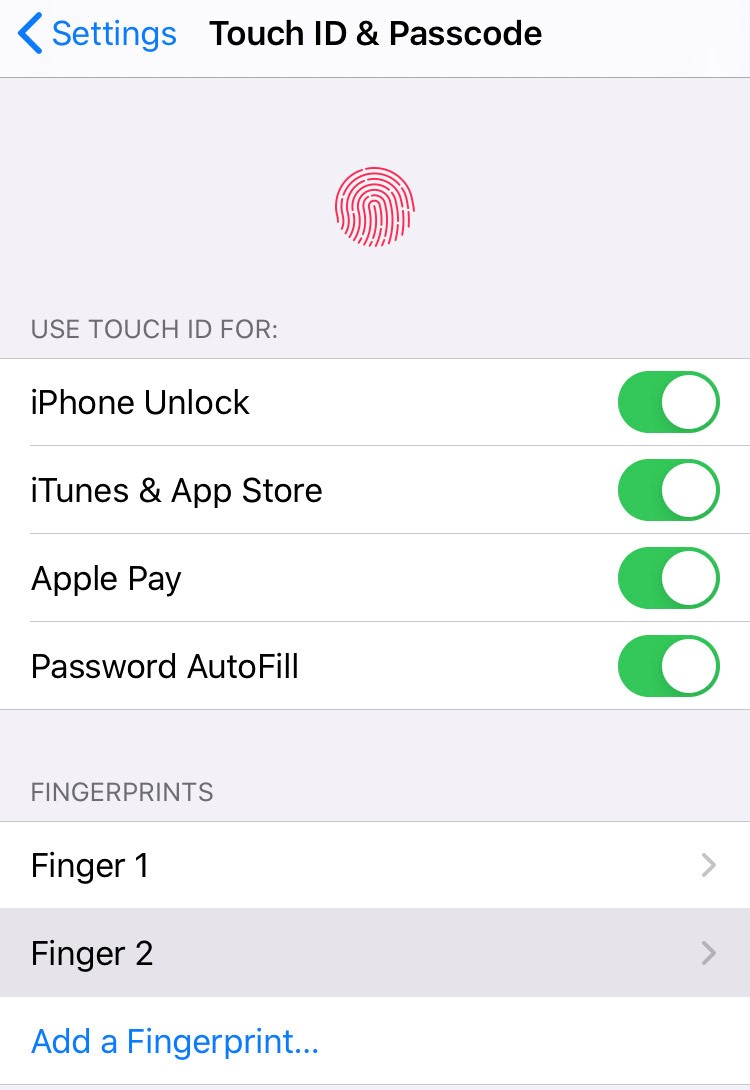
Depending upon your mobile model you may have either a fingerprint or facial biometric. Biometrics can be used to unlock the device as well as authenticate you to different apps.
To configure:
1. Go to the Settings
2. Scroll down and select either Face ID & Passcode or Touch ID & Passcode (depending on the model of your device)
3. Enable the slider so that it is green for the options which you want to use the biometric for authentication. I recommend at least consider using it for unlocking the device which should be the first option listed.
4. Add your biometric in the section below, being either Face ID or Fingerprints. (Note that more than one biometric can be added for the device allowing either multiple people or multiple "fingers" to authenticate your device.)
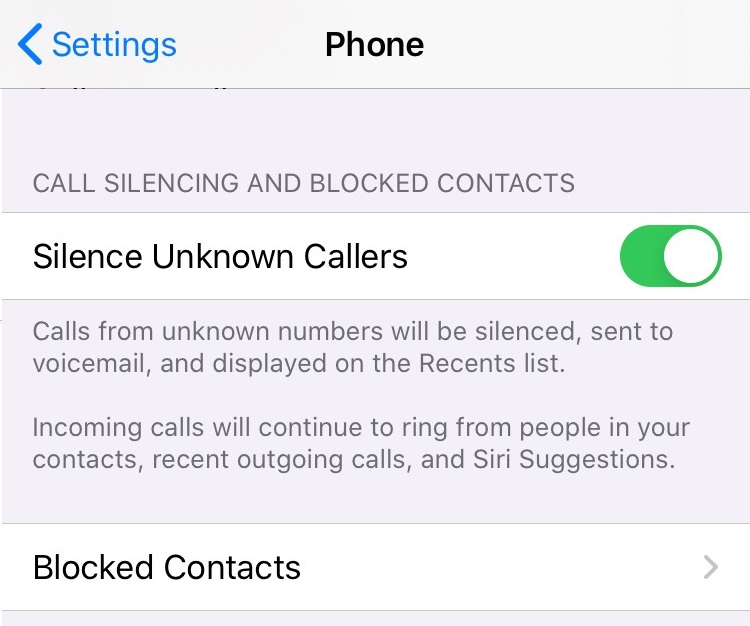
Block unknown caller feature
This is a newer feature on iOS and is very cool. In essence, enabling this feature will establish a known good whitelist of phone numbers on your device to accept calls from. If the number calling the device is not on that list the phone will silence the call and send it directly to voicemail. The whitelist is made up of phone numbers in the device contact list as well as recently called outbound phone numbers. Why enable this? It will give you the ability to ignore spam phone calls.
To configure:
1. Go to the Settings menu on your device
2. Scroll down and select Phone
3. Enable the slider for Silence Unknown Callers under the "Call Silencing and Blocking Contacts" menu
Disable not disconnect from WiFi and Bluetooth when not in use
iOS offers a convenience menu accessible on the device even when it is locked called "Control Center."
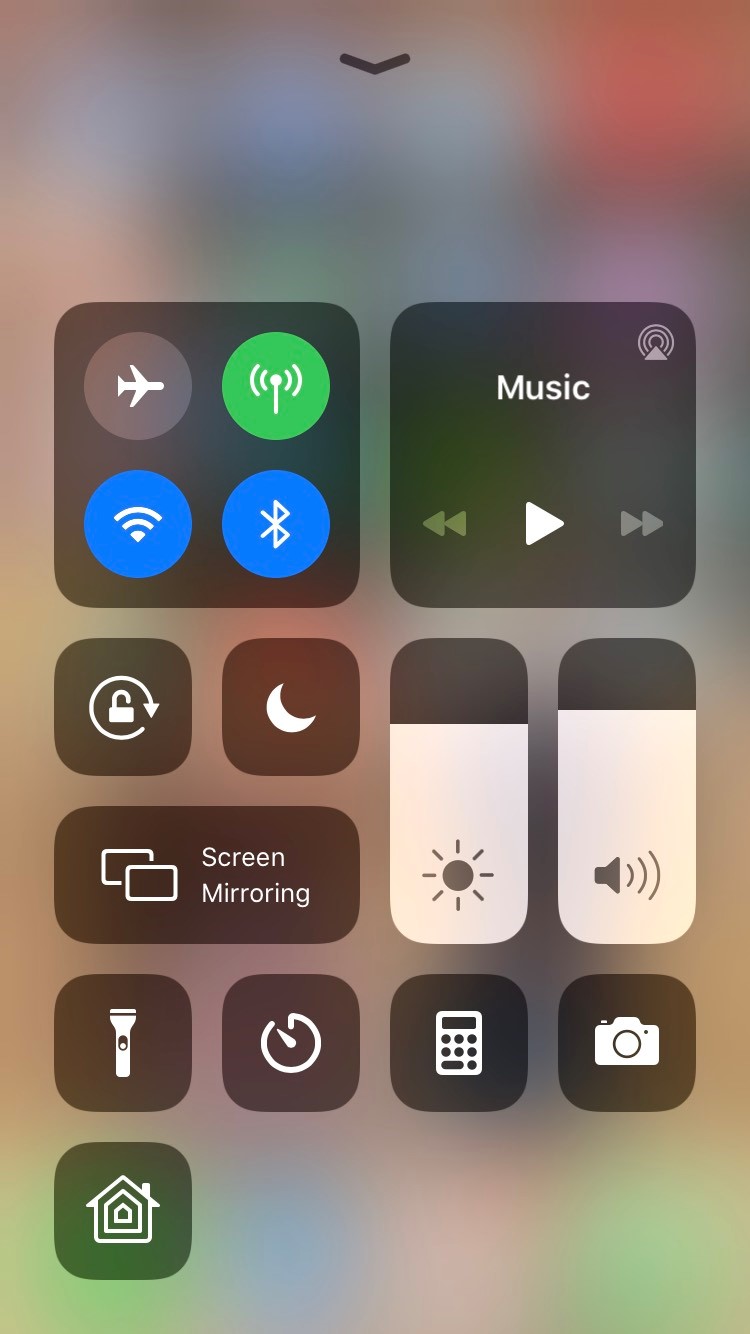
As you can see above, Control Center offers you the convenience to disconnect your WiFi and Bluetooth as well as place your phone in airplane mode. While this menu is a convenient way to control your device quickly, it does not actually disable WiFi but rather disconnects it. This means that WiFi is still enabled in the Settings menu while disconnected and still searching for wireless networks to join which can be exploited by attackers.
To properly turn off WiFi when not in use you should:
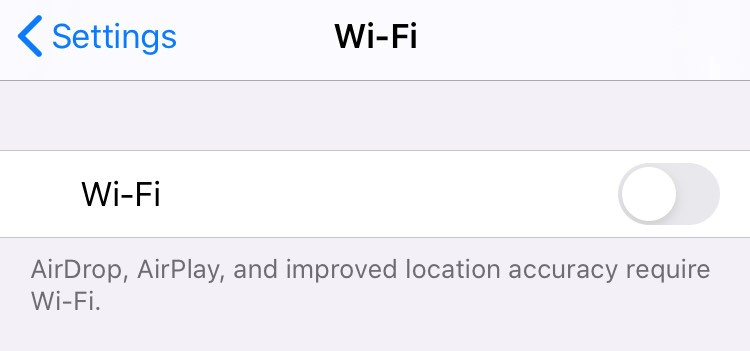
1. Go to the Settings menu on your device
2. Scroll down and select Wi-Fi
3. Ensure the slider is set to the left, to the OFF position
Disabling iCloud by default
Unless you want to use iCloud as a cloud storage provider I would disable this feature on the device. It will create another attack vector for malicious actors to attempt to get your private information, pictures, etc.
To configure:
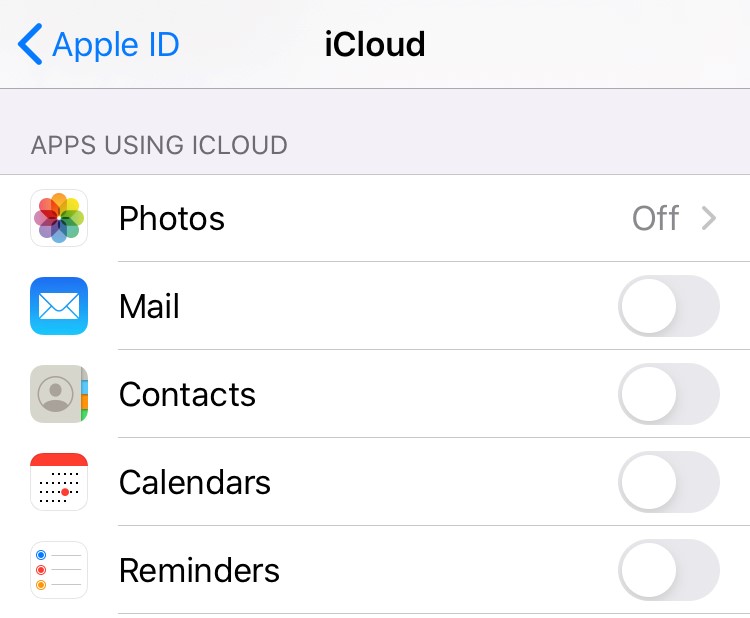
1. Go to the Settings menu on your device
2. Select Passwords & Accounts
3. Select iCloud under "Accounts"
4. Select iCloud
5. Ensure the sliders of anything you do not want synced to iCloud is set to the OFF position
Disabling services invasive to privacy
Whether you have an android or iOS device it is tracking you. On iOS there are a number of features you may want to consider disabling if you are privacy conscience.
Location Services
To configure:
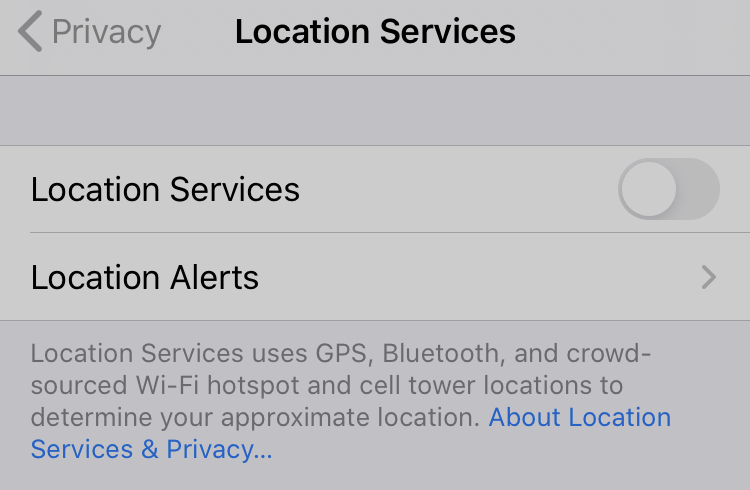
1. Go to the Settings menu on your device
2. Select Privacy
3. Select Location Services and ensure the slider is set to the OFF position
Analytics
To configure:
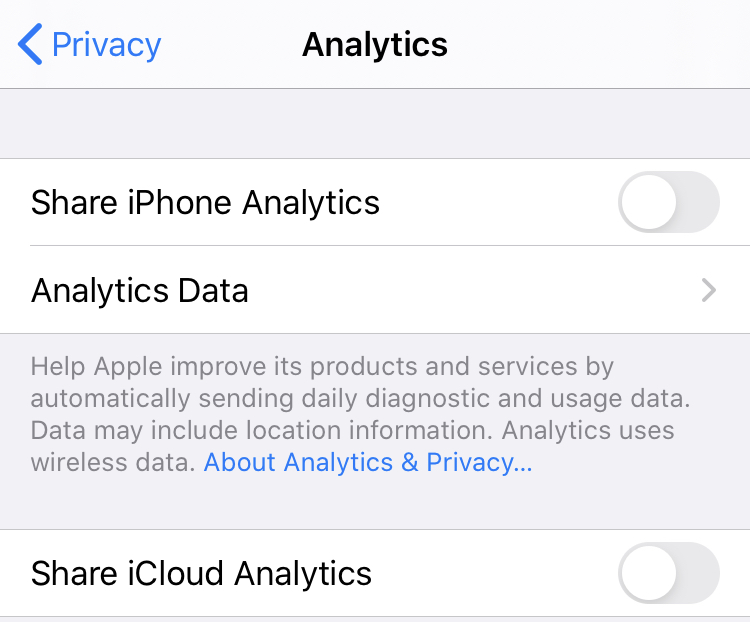
1. Go to the Settings menu on your device
2. Select Privacy
3. Select Analytics and ensure the slider is set to the OFF position for both iPhone Analytics and iCloud Analytics
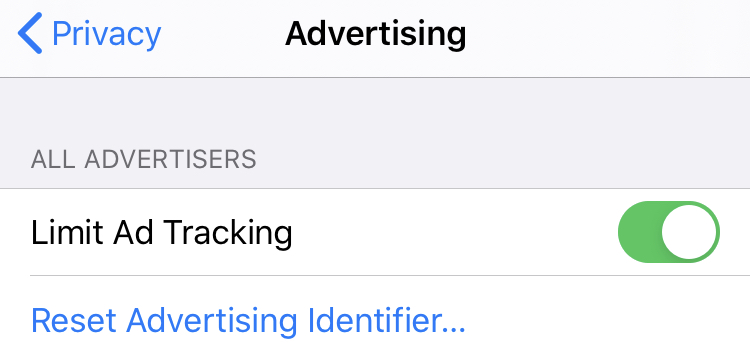
Advertising
To configure:
1. Go to the Settings menu on your device
2. Select Privacy
3. Select Advertising
4. Under the All Advertisers menu ensure the Limit Ad Tracking slider is set to the ON position
As the use cases for mobile devices continue to grow and replace the traditional desktop OS, a secure device configuration is key. In taking into account the current device marketplace and their OS ecosystems, iOS is the most secure option available among mainstream manufactures. If using iOS, there are a number of security minded features you can take advantage of as well as a items you many want to consider living without in order to protect your privacy while using the device. Following the steps outlined in the thought above should hopefully help you enable the security on your device without sacrificing too much in the way of user experience.
Resources Consulted
[1] Fidlee. (2013). Android Support vs iOS Support. Retrieved from Article Link.
Tags
Security Vulnerabilities IDS/IPS Malware Ethical Hacking Policies PowerShell Python Splunk Mobile Cloud Script PKI Firewall Router Vulnerability Management



